Hey there, tech-savvy friend! Let's dive into the world of securely connecting remote IoT devices to AWS VPC. If you're reading this, chances are you're already knee-deep in the cloud game or at least curious about it. AWS has become the go-to platform for businesses looking to scale their IoT infrastructure. But hey, let's not sugarcoat it—securing these connections is no walk in the park. In this guide, we’ll break down everything you need to know to make sure your IoT devices are as safe as Fort Knox.
Now, why should you care about securely connecting remote IoT to AWS VPC? Well, think about it like this: your IoT devices are like little spies out in the field, collecting data and sending it back home. If they get compromised, it’s like giving away the crown jewels. This article will help you lock down those devices and ensure your data stays where it belongs—securely within your AWS environment.
Before we dive deeper, let’s set the stage. Whether you're managing a fleet of smart thermostats or running an entire smart city, the principles remain the same. You want to make sure that your IoT ecosystem is not only efficient but also protected from prying eyes. So, buckle up, because we’re about to take you on a journey through the ins and outs of secure IoT connections in AWS.
- Mastering Remote Iot Vpc Network Aws Your Ultimate Guide
- Raspberry Pi Remoteiot Free The Ultimate Guide For Your Smart Projects
Table of Contents
Overview of Securely Connecting Remote IoT VPC AWS
Understanding the AWS VPC Architecture
Key Security Measures for IoT Devices
- Unveiling Filmyflywin 2025 Your Ultimate Hub For South Bollywood Hollywood And Hindi Animation
- Erome Jellybean The Ultimate Guide To Understanding The Phenomenon
Encryption Techniques for Secure IoT Connections
Setting Up a Secure Network in AWS VPC
Best Practices for IoT Security
Monitoring and Logging IoT Traffic
Tools and Services for IoT Security in AWS
Real-World Scenarios and Use Cases
The Future of IoT Security in AWS
Overview of Securely Connecting Remote IoT VPC AWS
Alright, let’s kick things off with the basics. Securely connecting remote IoT to AWS VPC is all about creating a fortress-like environment for your devices. Think of it as building a digital moat around your kingdom. AWS VPC (Virtual Private Cloud) acts as the backbone of your IoT infrastructure, providing a secure and isolated network where your devices can communicate freely.
Here’s the thing, though—IoT devices are notorious for being vulnerable to attacks. They’re often deployed in remote locations with minimal oversight, making them easy targets for hackers. That’s why it’s crucial to implement robust security measures from the get-go. By leveraging AWS’s powerful tools and services, you can create a secure connection that keeps your data safe and your devices humming along smoothly.
Why AWS VPC Is Essential for IoT Security
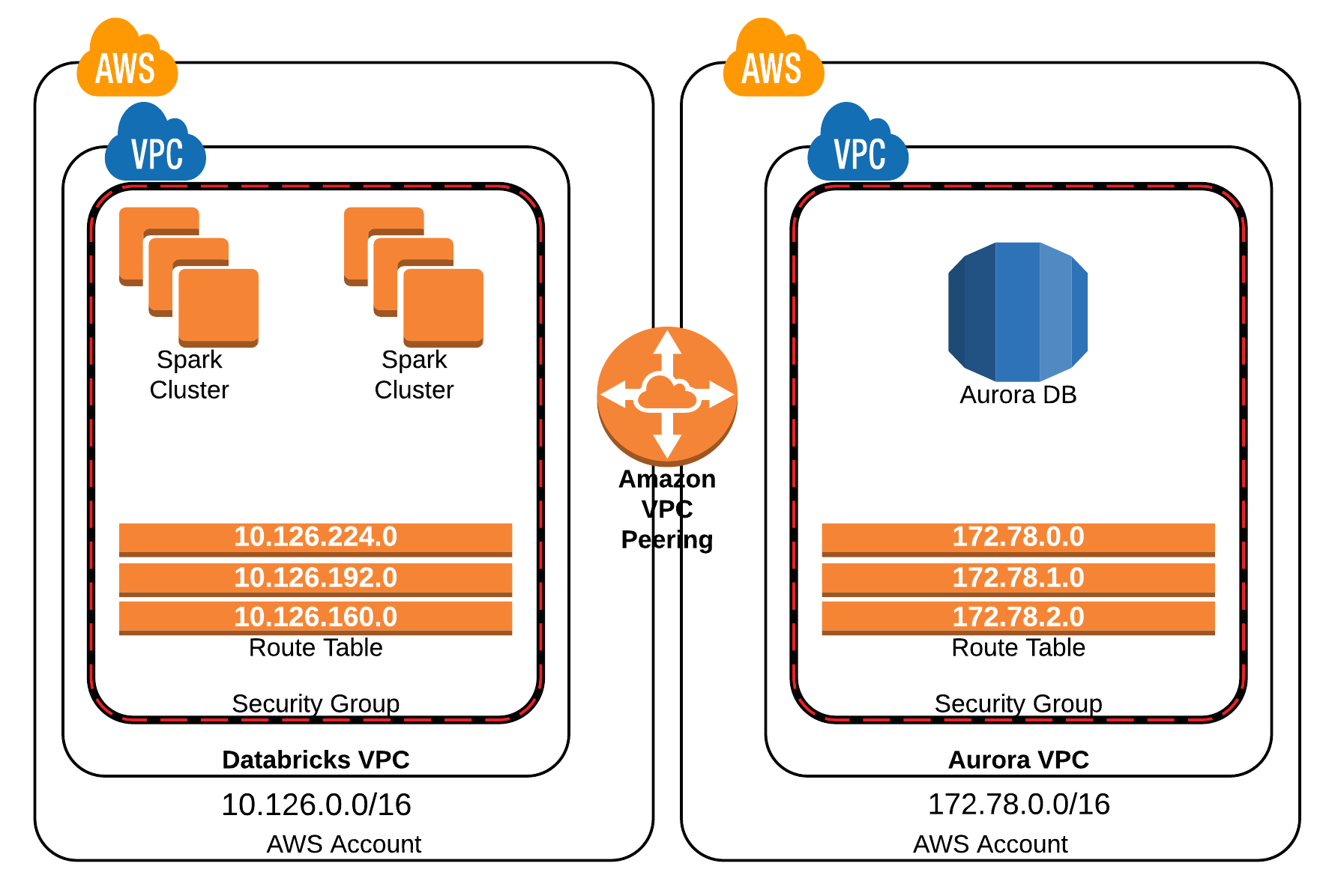
Let’s talk about why AWS VPC is the golden ticket for securing your IoT devices. AWS VPC allows you to define a virtual network in the cloud, giving you complete control over how your devices interact with each other and the outside world. With features like private subnets, security groups, and network access control lists (NACLs), you can fine-tune your security settings to fit your specific needs.
For example, you can set up a private subnet for your IoT devices, ensuring that they can only communicate with other devices within the same network. This reduces the risk of unauthorized access and keeps your data safe from prying eyes. Plus, with AWS’s scalable infrastructure, you can easily expand your IoT network as your business grows without compromising security.
Understanding the AWS VPC Architecture
Now that we’ve covered the basics, let’s dive into the architecture of AWS VPC. Think of AWS VPC as a digital blueprint for your IoT network. It’s made up of several key components, each playing a vital role in ensuring the security and efficiency of your IoT devices.
Key Components of AWS VPC
- VPC Subnets: These are sections of your VPC that allow you to segment your network into smaller, more manageable pieces. You can create public subnets for devices that need internet access and private subnets for devices that don’t.
- Security Groups: Think of these as virtual firewalls for your devices. They control inbound and outbound traffic at the instance level, ensuring that only authorized traffic is allowed through.
- Network Access Control Lists (NACLs): These act as an additional layer of security, controlling traffic at the subnet level. They’re like bouncers at a club, deciding who gets in and who doesn’t.
By understanding these components and how they work together, you can create a secure and efficient IoT network that meets your business needs.
Key Security Measures for IoT Devices
Let’s talk about the nitty-gritty of securing your IoT devices. Security isn’t just about setting up a VPC and calling it a day. It’s an ongoing process that requires constant vigilance and attention to detail. Here are some key security measures you should implement to keep your IoT devices safe:
Authentication and Authorization
One of the most important aspects of IoT security is authentication and authorization. You need to make sure that only authorized devices and users can access your network. AWS offers several tools for this, including AWS Identity and Access Management (IAM) and AWS Cognito.
With IAM, you can create and manage user accounts and permissions, ensuring that each user has the appropriate level of access. AWS Cognito, on the other hand, allows you to add user sign-up, sign-in, and access control to your IoT applications.
Encryption Techniques for Secure IoT Connections
Encryption is another crucial component of IoT security. By encrypting your data, you ensure that even if it falls into the wrong hands, it remains unreadable. AWS offers several encryption options for securing your IoT connections:
Using AWS KMS for Encryption
AWS Key Management Service (KMS) is a managed service that makes it easy to create and control the encryption keys used to encrypt your data. With AWS KMS, you can encrypt your data at rest and in transit, ensuring that it remains secure throughout its lifecycle.
For example, you can use AWS KMS to encrypt data stored in Amazon S3 or data transmitted between IoT devices. This adds an extra layer of security to your IoT network, making it much harder for attackers to gain access to your sensitive information.
Setting Up a Secure Network in AWS VPC
Now let’s talk about setting up a secure network in AWS VPC. This is where the rubber meets the road, so to speak. By configuring your VPC correctly, you can create a secure and efficient network that meets your IoT needs.
Configuring Security Groups and NACLs
Security groups and NACLs are your first line of defense when it comes to securing your IoT network. By configuring them correctly, you can control who has access to your devices and what kind of traffic is allowed.
For example, you can create a security group that only allows traffic from specific IP addresses or ports. You can also create NACLs that block all incoming traffic except for traffic from trusted sources.
Best Practices for IoT Security
Let’s wrap up this section with some best practices for IoT security. These are the things you should be doing on a regular basis to ensure the security of your IoT devices:
- Regularly update your devices and software to patch any vulnerabilities.
- Monitor your network for suspicious activity and take action if necessary.
- Implement multi-factor authentication for added security.
By following these best practices, you can create a secure and resilient IoT network that can withstand even the most sophisticated attacks.
Monitoring and Logging IoT Traffic
Monitoring and logging are essential for detecting and responding to security threats. By keeping an eye on your IoT traffic, you can quickly identify and respond to any suspicious activity.
Using AWS CloudWatch for Monitoring
AWS CloudWatch is a powerful tool for monitoring your IoT devices and network. It allows you to collect and track metrics, collect and monitor log files, and set alarms for when certain conditions are met.
For example, you can use CloudWatch to monitor the CPU usage of your IoT devices or track the number of failed login attempts. This gives you real-time visibility into your network and helps you quickly identify and respond to any potential security threats.
Tools and Services for IoT Security in AWS
AWS offers a wide range of tools and services for securing your IoT devices. Here are some of the most important ones:
- AWS IoT Core: This is the backbone of AWS’s IoT platform, providing secure and reliable communication between your devices and the cloud.
- AWS IoT Device Defender: This service helps you audit and enforce security policies for your IoT devices, ensuring that they remain secure over time.
- AWS WAF: This web application firewall helps protect your IoT applications from common web exploits.
By leveraging these tools, you can create a comprehensive security strategy that covers all aspects of your IoT network.
Real-World Scenarios and Use Cases
Let’s take a look at some real-world scenarios where securely connecting remote IoT to AWS VPC has made a difference:
Smart Agriculture
In the world of smart agriculture, IoT devices are used to monitor soil moisture, weather conditions, and crop health. By securely connecting these devices to AWS VPC, farmers can make data-driven decisions that increase yield and reduce waste.
Smart Cities
Smart cities use IoT devices to monitor traffic patterns, air quality, and energy usage. By securely connecting these devices to AWS VPC, city planners can create more efficient and sustainable urban environments.
The Future of IoT Security in AWS
As IoT continues to evolve, so too will the tools and techniques used to secure it. AWS is constantly innovating in this space, introducing new features and services that make it easier to secure your IoT devices.
In the future, we can expect to see more advanced machine learning algorithms being used to detect and respond to security threats in real-time. We may also see the development of new encryption techniques that make it even harder for attackers to gain access to sensitive data.
Conclusion
And there you have it, folks! A comprehensive guide to securely connecting remote IoT to AWS VPC. By following the steps outlined in this article, you can create a secure and efficient IoT network that meets your business needs.
Remember, security is an ongoing process. Stay vigilant, keep your devices and software up to date, and regularly monitor your network for suspicious activity. And if you’re looking for more tips and tricks, be sure to check out our other articles on IoT security.
So, what are you waiting for? Go out there and secure those IoT devices! And don’t forget to leave a comment or share this article with your friends. Together, we can make the IoT world a safer place for everyone.


Detail Author:
- Name : Mr. Daryl Hessel
- Username : macejkovic.miguel
- Email : von.columbus@pagac.com
- Birthdate : 1976-08-30
- Address : 25335 Feil Light Apt. 575 Lake Elenora, VT 59503
- Phone : +15867694669
- Company : Gleason-Auer
- Job : Command Control Center Officer
- Bio : Voluptatem reprehenderit voluptates voluptates corporis. Dolorem quia quidem quis soluta. Aliquam incidunt fugit minima illo.
Socials
instagram:
- url : https://instagram.com/clementina3693
- username : clementina3693
- bio : Voluptate omnis sint earum repellat. Quos distinctio fuga repellendus porro at.
- followers : 2447
- following : 1662
facebook:
- url : https://facebook.com/clementina_dev
- username : clementina_dev
- bio : Et nostrum ipsa ex similique. Voluptas eaque autem a ut.
- followers : 3570
- following : 494